Legacy Applications Webinar on Demand
Using Microsoft Window Virtual Desktop (WVD) to move your legacy business applications into the cloud.
Still Using Obsolete Apps? You Are Not Alone
If your organisation is still regularly using an application that has become outdated and insecure, then you can take some comfort from the knowledge that you are not alone.
From factories to hospitals, there are applications in daily use that have no upgrade path because the software was bespoke, or the publisher no longer exists and redeveloping the application for a limited number of users is not financially worthwhile.
Similarly, sometimes there is no business benefit to upgrading. The application does exactly what you need it to do and upgrading to the latest version can cost a small fortune.
But that doesn’t mean you can do nothing about it.
A Stable, Secure and Long-Lasting Solution
Any piece of software has both support challenges and security risks and Droplet Computing’s containerisation technology, in partnership with APPTechnology, allows you to provide a stable, secure and long-lasting platform for those applications in your environment.
Droplet containers will support USB, serial, COM ports and LPT ports with no additional licencing cost. Moreover, you can very quickly be using outdated applications in a scalable, multi-session Windows 10 infrastructure in the cloud using Windows Virtual Desktop.
Unique, Award-Winning, Patented Container Technology
“When we say containers, everyone thinks of Docker,” says Chief Operating Officer, Barry Daniels. “We are not that.”

Droplet Computing is a worldwide patented container technology and the only company to win back-to-back awards from the British Computer Society. Droplet divorces an application from its underlying operating system, putting it into a container, “wrapping a security blanket around it” and then allowing you to deploy that cross-platform where it needs to run.
“We sell security, compatibility and compliance,” Barry continues. “The challenge that you have out there typically is with legacy applications tied to an old version of .net or Java or an old version of IE. Windows Virtual Desktop is a great way of moving that forward but then how do you get your legacy applications there? Droplet it is the answer.”
A Droplet container does not require your legacy application to be refactored, sequenced or packaged. And no back-end infrastructure is needed, so you can transfer your apps to the cloud at no additional cost.
“We take security seriously,” says Barry, “and we don’t rely on just us saying that we are secure.”
Pen Tested by NCC Group
Droplet was audited by NCC group plc, who carried out penetration testing.
“We put some really insecure things inside our container,” recalls Barry. “IE8 running Java 1.6 through a JInitiator app that really would be very vulnerable. We said to the NCC Group: ‘Go ahead, do your worst, go hack’. They couldn’t hack in from outside of the container system.”
“We then took a step further,” Barry explains. “They then took a compromised host machine and tried to crack into this vulnerable software from inside a compromised host and still couldn’t get inside.”
How Droplet Works
When using Windows Virtual Desktop, The Virtual Cloud Edition of Droplet is deployed. “That takes care of the compatibility layer for us,” explains Barry, “and talks from the host system to our container and enables bi-directional traffic to be translated via our software. Then we attach the container image itself that bolts onto that application. This can be deployed very simply.”
“You create a central, golden image, DCI-X for Windows XP or older applications, right back to DOS, or DCI-M for Windows 7 to 10 applications. Once locked inside that you create a policy engine, you create all of the governance inside one centralised image and then you can deploy it a hundred times or a thousand times - it scales particularly well.”
Droplet in Action
Droplet supports two different runtime modes: the user mode and the service mode.
The decision about which mode to use depends on whether the application will be used frequently or infrequently.
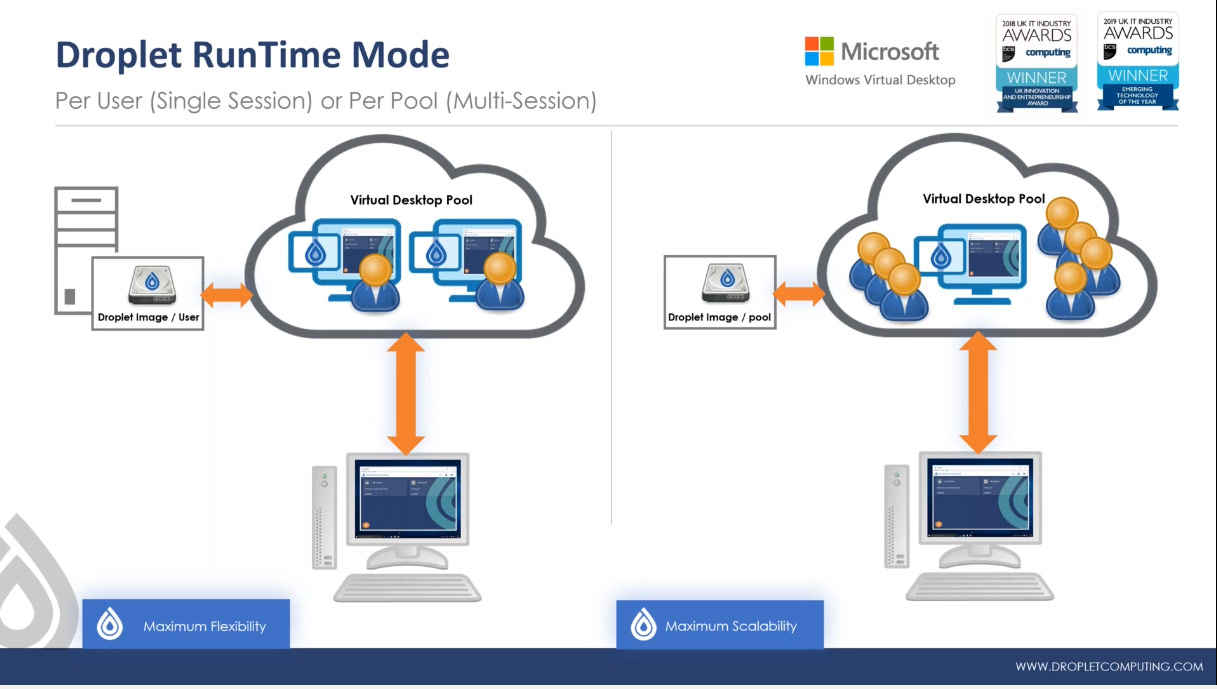
Droplet Computing containers - two runtime modes explained
User Mode
In the user mode, it’s the user who starts up the container and this works quite well for environments where the containerised application that is used relatively infrequently - maybe just once a day for an hour, or once a quarter to run some sort of batch process or indeed a situation where you need access to the legacy system just for compliance or audit reasons.
In the user mode, the user gets their own container. This gives them maximum flexibility. They can customise the container however they want.
Service Mode
For applications that are used every day, all day, highly frequently, the service mode is recommended. In the service mode, the container starts when the WVD instance starts, and it “services up” applications for many users.
In the service mode, the container can be compared to the way Microsoft has allowed Windows 10 to be multi-session. Like old-style terminal servers or Remote Desktop Session Host (RDSH), the container inside that virtual desktop pool can also be multi-session. So, multiple users can connect to the same Windows 10 desktop and multiple users can pull out applications from the container.
“This scales very well for a high density of users and high concurrency rates,” explains Michelle Laverick, Droplet Computing’s Chief Technologist. “If you are limited by Total Cost of Ownership (TCO) and you need to get maximum bang for your buck, the multi-session per-service mode is for you.”
“In terms of the resources that are available to the two different modes,” continues Michelle, “we tend to go for the 32-bit container in the per user mode, which has a maximum of two container CPUs and 4 GB of memory, although often you can get away with one container CPU and 2 GB of memory. With the per service mode we tend to recommend the 64-bit container, which has a massive four container CPUs and 192 GB of memory. You can carve out of your Windows 10 instance a chunk of memory purely for supporting your legacy applications, based on the frequency with which the applications are being accessed. If they are not being used very much, you don’t need much memory.”
Seamless User Experience
Of course, most end users know nothing about the underlying infrastructure that allows legacy apps to run on Windows 10.
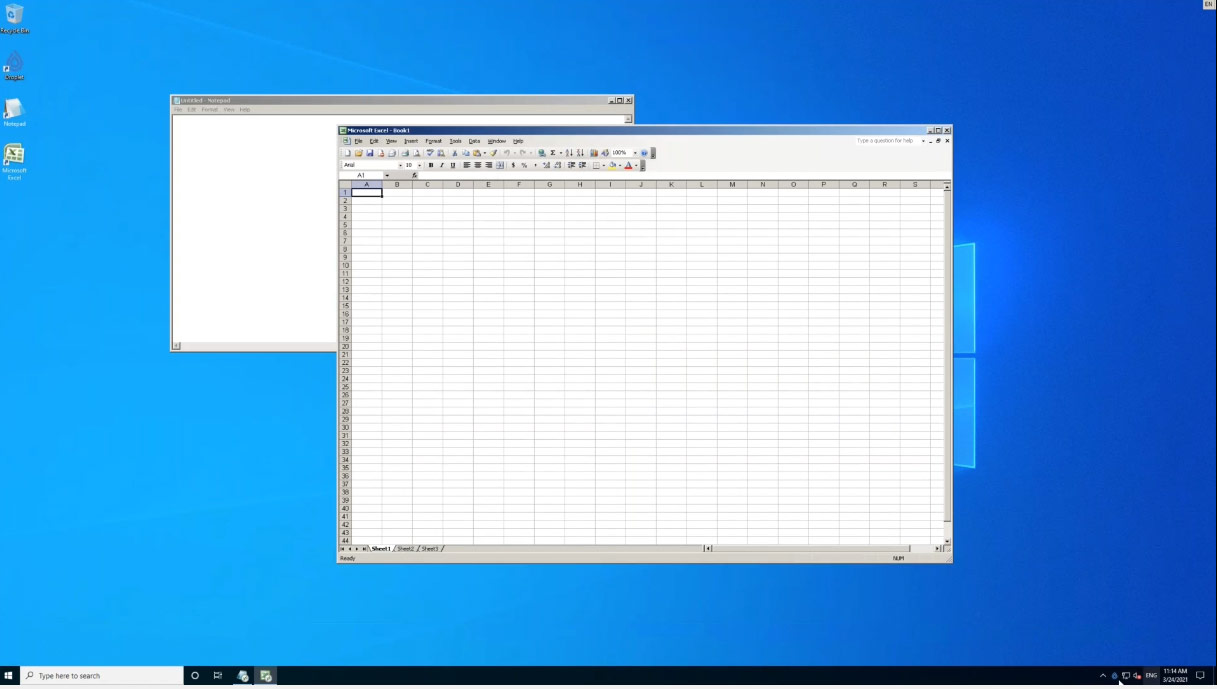
Seamlessly loading Excel 2003 in a container
“What users generally see on their desktop is what we call a Droplet Seamless App,” says Michelle. “The application floats on the desktop just like any other program and the end user has no idea that it is running in a container. They just double click a shortcut on their desktop and the application opens up.”
Administrator Interface
For the network administrator, a user-friendly front-end management application is provided so you can start up your container and install applications to it.
This UI contains a toolbox of utilities for the system administrator to do an installation. Seamlessly installing an application to the container appears to work exactly the same as when you install that application to a single PC.
Admin at Scale
The admin front-end is very useful when you’re setting up, but if you want to deploy applications at scale, you don’t really want to be interacting with the graphical UI for every single user. Fortunately, each user’s settings can be controlled by the four meta data files in the user’s profile: apps.json, the credentials file, the droplet.lic licence file and the “EULA accept” file. “That’s all you need in the world of WVD,” boasts Michelle.
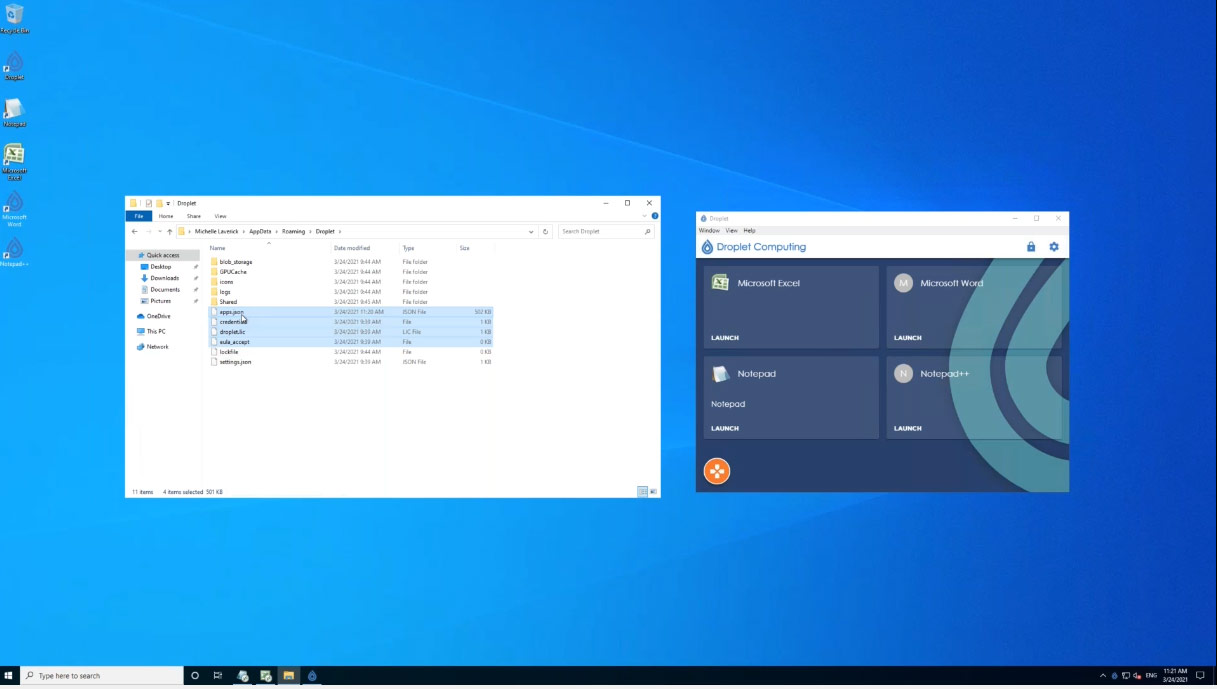
Deployment of containers at scale using just four user files
“So, when each user logs on, they will get exactly the same user experience as everyone else as long as those files are in their profile,” Michelle continues. “And of course you can have many apps.json files on your network, so when Harry logs in, he will get his apps.json, which might show six applications, but when Judy from the accounts department logs on, she gets an apps.json file with eight applications. So deploying those files is a very fast and user-friendly way to set up large numbers of different users with different needs across an organisation.”
Legacy Application Management from APPtechnology
The combination of WVD and Droplet resolves the support and security challenges of a legacy application by moving it to Windows 10 and to the cloud, making it a much smarter application for deployment.
Trust your legacy apps to APPtechnology and very soon you will be able to free yourself from outdated, vulnerable old hardware and operating systems without compromise, continuing to deliver a consistent experience to end users on virtually any device.
FREE WEBINAR available on demand
APPtechnology and Droplet show you how you can leverage WVD to move legacy applications from your estate securely into the cloud. Remove security issues, save on support costs and benefit fully from Microsoft Modern Management technologies.
Examples of outdated/legacy business applications running securely in the cloud
Watch the free 25 minute webinar on demand
Sign up for our mailing list to find out about future events and webinars and get instant access to the Legacy Applications webinar. Find out how APPtechnology can extend the life of your legacy applications securely and cost-effectively.
In submitting this form you agree to our terms and conditions